What is split tunneling in cyber security?
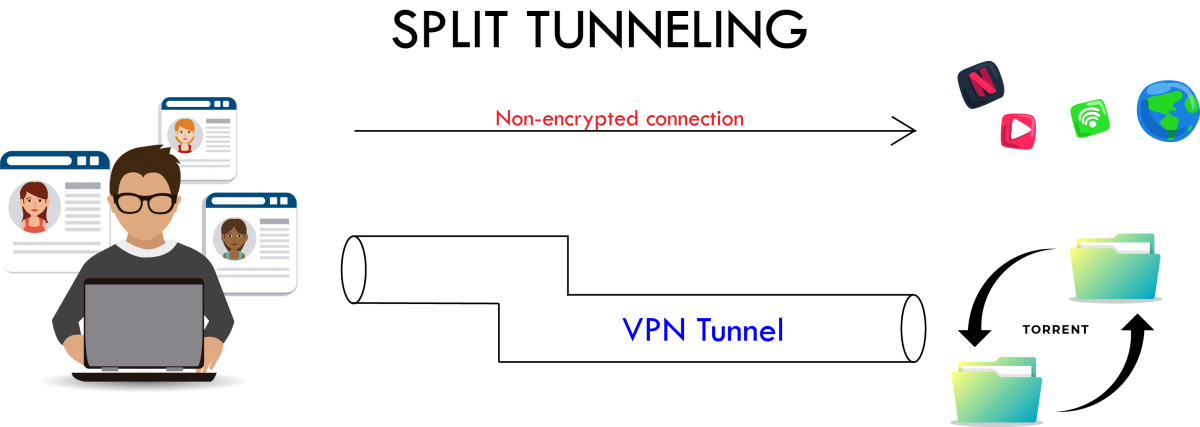
Split tunneling is often bantered about in cybersecurity. What does it really mean? Split tunneling diverts some data through an encrypted VPN connection while allowing other apps and data to have direct access to the Internet. That’s relevant for remote access-type VPNs (like those used for working from home) where your computer is connected directly to a remote network at the office.
All VPNs are a network “tunnel.” Say your computer has information it wants to send to a remote device. Without a VPN, it sends that information into the network and lets it hop from device to device until it reaches its destination.
With a VPN, the computer first sends the information in encrypted form to a VPN termination point. The original information is extracted and decrypted and sent along its way to the ultimate destination as if it had only gone one hop instead of the dozens of hops encrypted information travels.
Split tunneling represents the best of both worlds: the speed and performance of an unencrypted link, and the data security when and where needed.
The pros and cons of split tunneling
Split tunneling alleviates bottlenecks and conserves bandwidth as Internet traffic does not have to pass through the VPN server. It’s advantageous when a user works at a supplier or partner site and needs access to resources on both private and public networks.
Consider the alternative where everything must pass through the VPN tunnel. If you are streaming a webinar or taking part in a video conference, a substantial amount of information is encrypted and sent through the VPN.
This detour means that information that has nothing to do with the corporate network is traversing that corporate internet link twice—it’s slower, it causes congestion, and it’s a nightmare for your network monitoring solution to parse.
Another disadvantage to tunneling everything is that it can prevent your computer from talking to your printer or other local devices.
Split tunneling addresses these issues by allowing VPN users to direct their non-corporate traffic to the Internet without involving corporate links or equipment.
The cons of split tunneling can be summed up in two words: security compromises. There are compelling reasons why many companies accept the performance hit by driving all traffic through their VPN connection: It allows them to block known malware and control access to inappropriate sites on the Internet.
If the corporate VPN redirects Internet traffic through a central point, it can also route that traffic through system security devices. For instance, intrusion prevention devices (IPS) look for malicious content. Because very few end-users have the same security infrastructure on their home networks, forcing all that traffic through the corporate infrastructure essentially places your home network behind the corporate perimeter, which is arguably safer.
Or, for those on a public Wi-Fi network in a coffee shop or hotel, devices on the local network should be treated as hostile by default. They could be snooping on your traffic and trying to break into your computer over local protocols. Therefore, it makes sense to encrypt everything and send it to a central VPN host before forwarding it to the internet.
Security and split tunneling
The significant reason IT security pros cite for disabling split tunneling has to do with endpoint vulnerabilities. Attacks against corporate infrastructure typically begin by compromising an end user’s computer. From there, they exploit any trust relationships associated with that computer. They can also snoop on things you might type, like user IDs and passwords.
Exploiting this kind of vulnerability requires that the attacker has access to your computer while your computer has access to the corporate network. With split tunneling disabled, the corporate security infrastructure has a chance to intercept the attacker’s command and control traffic.
CMMC requirements regarding split tunneling
Per NIST SP 800-171 Rev 2 3.13.7 and CMMC SC.L2-3.13.7, the requirement for split tunneling is:
Prevent remote devices from simultaneously establishing non-remote connections with organizational systems and communicating via some other connection to resources in external networks (i.e., split tunneling).
Exactly what does this mean? The remote device is the laptop being used by an employee when they are not in their normal operating location. Home offices cannot be declared the normal operating location, because their home office then requires equivalent protections as your normal office space.
Organizational Systems: These are all the other systems in your system scope per NIST SP 800-171 para 1.1.
Non-remote connections with organizational systems occur when the VPN tunnel is established and creates an encrypted connection between the gateway and the user device that allows the remote device access to internal resources as if it was in the office.
Put simply, a company user, when not working in the office on the organization’s internal network, cannot access both internal assets via VPN services and external, untrusted information systems unless it goes through the organization’s firewalls. To meet the requirement, split tunneling must be disabled.
With split tunneling enabled, a remote hacker can compromise the laptop. The hacker then realizes there is a remote connection to the laptop’s organization. The hacker exploits that remote connection to exfiltrate data or tries to break into and control the organization’s systems internally.
With split tunneling disabled, when the user tries to go to the malicious website, the traffic goes up the VPN tunnel, and the VPN gateway’s firewall either blocks the traffic prior to the user connecting or the firewall detects the malicious traffic patterns and blocks the connection from going any further.

Should you use split tunneling for your organization’s security?
While speed and performance are tempting, security remains the top priority for many organizations. DTS, therefore, recommends a cloud-based Secure Access Service Edge (SASE) product to securely connect users, systems, and endpoints to applications and services anywhere. Our partner, Perimeter 81, offers one that allows companies to set up gateways wherever employees are working, around the world, to minimize network latency and scale up and scale down as needed.
DTS consults on security situations for organizations looking at best practices or required to comply with CMMC or other controls. To start the conversation, sign up for a free 30-minute consultation and start the conversation at our contact page.


