NIST SP 800-171 provides recommended requirements to federal agencies for protecting the confidentiality of controlled unclassified information (CUI) in non-federal systems and organizations. It is used as a voluntary best-practice cybersecurity framework for commercial firms working to protect their sensitive information, a standard for government contractors and subcontractors, and the foundation of the soon-to-be mandatory DoD cybersecurity program, CMMC.
NIST SP 800-171 Compliance
For contracts and organizations that require robust cybersecurity controls of their subcontractors, partners, or vendors, NIST SP 800-171 is the framework referenced in DFARS 252.204-7012. Claiming compliance with NIST SP 800-171 requires self-attestation – no third-party audit is needed.
NIST (National Institute of Standards and Technology) is a non-regulatory agency under the U.S. Department of Commerce. Its primary role is to develop standards (particularly for security controls) that apply to various industries. NIST SP 800-171 is shorter and simpler than NIST 800-53, from which its controls are derived.
The intent of the standard as it relates to DFARS 252.204-7012 is to encourage organizations to fully implement all 110 controls. However, there’s a bit of a loophole in that the publication only asks that “Nonfederal organizations describe, in a system security plan, how the security requirements are met or how organizations plan to meet the requirements and address known and anticipated threats…”
This means that organizations can claim compliance while acknowledging deficiencies and unimplemented security requirements if a plan exists to work on meeting them in the future.
Elements of NIST SP 800-171:
System Security Plan: The System Security Plan is the foundation of NIST SP 800-171 compliance. According to the standard, it must contain the system boundary, operational environment, how security requirements are implemented, and the relationships with or connections to other systems. NIST SP 800-171 allows organizations to document the system security plan and the plan of action as separate or combined documents.
Plans of Action & Milestones (POA&Ms): POA&Ms describe why an organization has not or cannot satisfy a requirement, the steps planned to address the deficiencies, and the date when the plan will be executed.
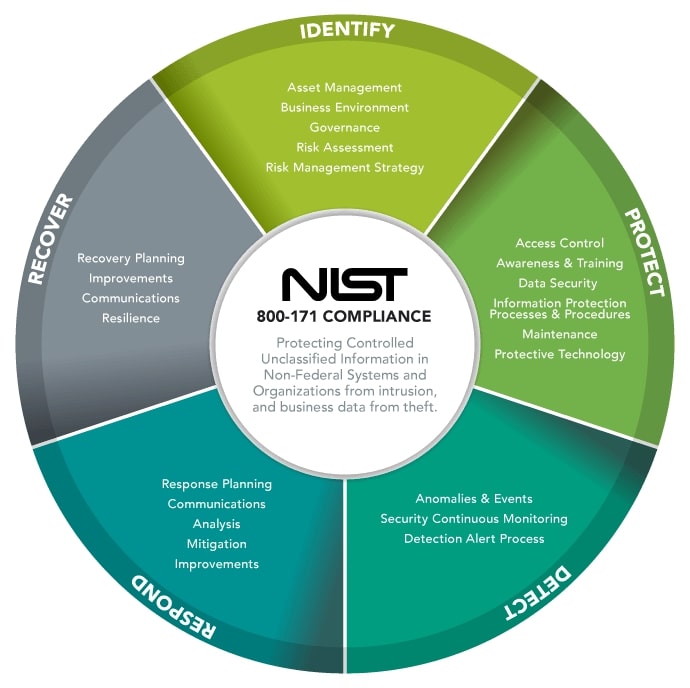
NIST SP 800-171 Scoring
Many contractors are asked to divulge their NIST SP 800-171 score or report it. This score reflects how many of the requirements are implemented prior to the contract award. The score is generated by using the NIST SP 800-171 DoD Assessment Methodology and ranges from a -203 to 110. The negative number exposes deficiencies/vulnerabilities.
NIST scores are reported to the Supplier Performance Risk System (SPRS) database, where other supplier information is stored. Here, contracting officers can verify that a company has a current score submitted prior to the contract award. The terms “self-assessment” and “assessment” may refer to this score.
NIST documentation should be updated annually or as needed, and the score should be updated in SPRS at least every three years. NIST SP 800-171 has been described as a living document, with contractors expected to follow any evolving requirements and controls. For example, it is currently on Revision 2 and NIST released Revision 3 for public comment on July 19, 2022.
What are NIST SP 800-171 requirements?
NIST 800-181 contains 110 controls in 14 control families aimed at keeping the confidentiality of CUI protected. To meet the standards, a company may need to invest in new software products, re-configure existing systems, implement stronger physical security controls, develop new internal processes, and monitor and document their system performance.
Following the NIST data security requirements helps prevent data loss, control insider threats, and address other cybersecurity challenges.

Requirement families of NIST SP 800-171
Each of the 14 requirement families within NIST SP 800-171 contain requirements related to that general security topic. The family organization of the standard attempts to make understanding the controls more straightforward for a company to self-assess and employ the requirements.
The 14 requirement families of NIST SP 800-171 are:
- Access Control: Deals with access to networks, systems, and information. 22 different requirements help to ensure that only authorized users access the system. Requirements also safeguard the flow of sensitive information within the network and provide guidance on network devices in the system.
- Awareness and Training: 3 requirements make up this section. Requirements include ensuring system administrators and users are aware of security risks and related cybersecurity procedures and that employees are trained to carry out security-related roles.
- Audit and Accountability: 9 requirements are in this family, focused on auditing and analyzing system and event logs. The requirements deal with the recording and storage of reliable audit records to allow for best practice analysis and reporting. Regular review of system security logs can help uncover and mitigate cybersecurity incidents.
- Configuration Management: These 9 requirements cover the proper configuration of hardware, software, and devices across the organization’s system and network. This domain of requirements also focuses on preventing unauthorized software installation and the restriction of nonessential programs.
- Identification and Authentication: This family of requirements safeguards authenticated users accessing the organization’s network or systems. The 11 requirements cover password and authentication procedures and policy and the reliable identification of users. Requirements ensure the distinction between privileged and non-privileged accounts is reflected in network access.
- Incident Response: 3 requirements cover the capability of the organization to respond to serious cybersecurity incidents. The requirements look for procedures in place to detect, contain, and recover a range of incidents. It includes proper training and planning, as well as regular testing of capabilities.
- Maintenance: These 6 requirements provide insight into best practices and network maintenance procedures. This includes the performance of regular system maintenance and making sure any external maintenance is secure and authorized.
- Media Protection: There are 9 security requirements to help organizations control access to sensitive media. Requirements cover best practice storage or destruction of sensitive information and media in both physical and digital formats.
- Personnel Security: 2 security requirements cover the safeguarding of CUI in relation to personnel and employees: the need for security screening of individuals and protecting CUI during termination or transfer of personnel, including scenarios such as the return of building passes or hardware and devices.
- Physical Protection: These 6 security requirements deal with physical access to CUI within the organization, including the control of visitor access to work sites and limited access to hardware, devices, and equipment.
- Risk Assessment: These 2 requirements cover the performance and analysis of regular risk assessments, including regularly scanning systems for vulnerabilities and keeping network devices and software updated and secure.
- Security Assessment: 4 requirements cover the development, monitoring, and renewal of system controls and security plans. By periodically reviewing security procedures, vulnerabilities across the organization are highlighted and improved.
- System and Communications Protection: These 16 requirements cover the monitoring and safeguarding of systems and the transmission of information. Requirements include the prevention of unauthorized information transfer and the denial by default of network communication traffic. Requirements also include best practice cryptography policies.
- System and Information Integrity: 7 requirements deal with monitoring and ongoing protection of systems within the organization, including processes for identifying unauthorized use of systems and the monitoring of system security alerts.
What’s the difference between NIST SP 800-171 compliance and CMMC?
Due to the lack of certification, the Department of Defense (DoD) found that contractors were claiming to uphold all of the NIST SP 800-171 standards. However, in reality, they were not. DoD decided it was necessary to develop a certification process to ensure that contractors were compliant with a set of cybersecurity controls based on the type of information to which the organization has access: The Cybersecurity Maturity Model Certification (CMMC).
The CMMC is designed to set protection standards for companies in the defense industrial base (DIB). By incorporating cybersecurity standards into acquisition programs, CMMC provides the DoD with the assurance that contractors and subcontractors are meeting DoD’s cybersecurity requirements.
This latest version of CMMC contains a tiered model with three levels. Level 1 is considered Foundational. Level 2 is Advanced. Level 3 is Expert. CMMC 2.0 Level 2 contains 110 practices, each of which directly maps to the 110 controls found in NIST SP 800-171. Level 3 also contains all the controls mapped from NIST 800-172. DIB contractors can self-attest to Level 1 and select Level 2 contracts. DoD has said most Level 2 contracts will require the Cyber AB 3rd Party Certification, and all Level 3 Controls will require a certification from an assessment conducted by the DoD itself.
In the previous version of CMMC, a company could not receive a certification if it had any deficiencies. In the latest version, POA&Ms are allowed, but only select controls may be on them, and they must be closed within 6 months of the certification assessment.
At a glance, CMMC looks a lot like NIST SP 800-171 in terms of the required security requirements. In fact, all 110 NIST SP 800-171 controls can be found in CMMC Level 2. One difference to note is that CMMC uses different vocabulary. Instead of “controls” or “families” it uses “domains” and “practices.” The scoping for a CMMC assessment is also slightly different from the scoping required by various federal agencies.
As the industry waits for final answers and dates from the Cyber AB, formerly the CMMC Accreditation Body, companies in the DIB are encouraged to get started on NIST SP 800-171 compliance. Not only will NIST compliance cover a huge portion of the CMMC assessment, but it’s also the current contractual requirement under DFARS clause 252.204-7012.

Consult DTS
To assess where your company is currently standard with NIST SP 800-171, and to prepare for CMMC compliance, contact DTS.
DTS provides tailored, scalable cyber solutions for small and medium-sized organizations. We use top resources and the expertise of talented individuals with a passion for excellence to help protect our clients’ people and data.
Our approach is consultative and education oriented. You can feel confident that your DTS solution is strong, reliable, and helping to drive a culture of compliance. Choose DTS for security reviews and assessments, remediation, managed services, licenses, and fractional CIO services. Visit DTS website: Contact page to schedule a consultation call.


